No one questions the need for cybersecurity these days. With attacks coming on a daily basis, the question today is “how do I secure” rather than “why should I secure” or “do I need to secure at all.”
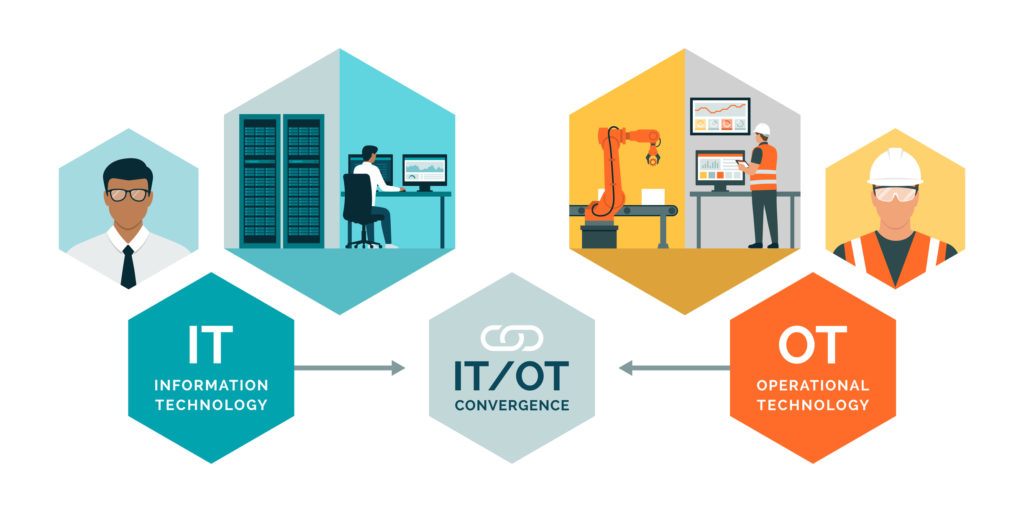
What’s less understood is the difference between securing at the OT (operational technology) level versus securing at the IT (informational technology) level. First, lets the define the two terms. Essentially, IT is responsible for managing the flow of information (data), while OT deals with the computers or other machinery that make use of that information. A simple analogy is that IT is the office while OT is the factory floor. Both are vital to an operation and must work collaboratively.
Keep in mind that the OT equipment isn’t necessarily housed under one roof. It could be spread out, in a smart building or even throughout a smart city or campus. The equipment could be used for manufacturing, energy generation, or in the agriculture space. The proliferation of hardware makes security more difficult, but no less important. A hacker accessing a single entry point could potentially gain access to the entire network.
An Embedded Computer to Drive the OT
An example of a hardware platform that’s used in energy or agriculture applications is the WINSYSTEMS’ PX1-C441 single board computer (SBC), designed to a PC/104 form factor. The SBC features the latest generation Intel Apollo Lake-I dual- or quad-core SoC processors for processing embedded workloads. And users can easily expand the SBC’s functionality through its PCIe/104 OneBank expansion.
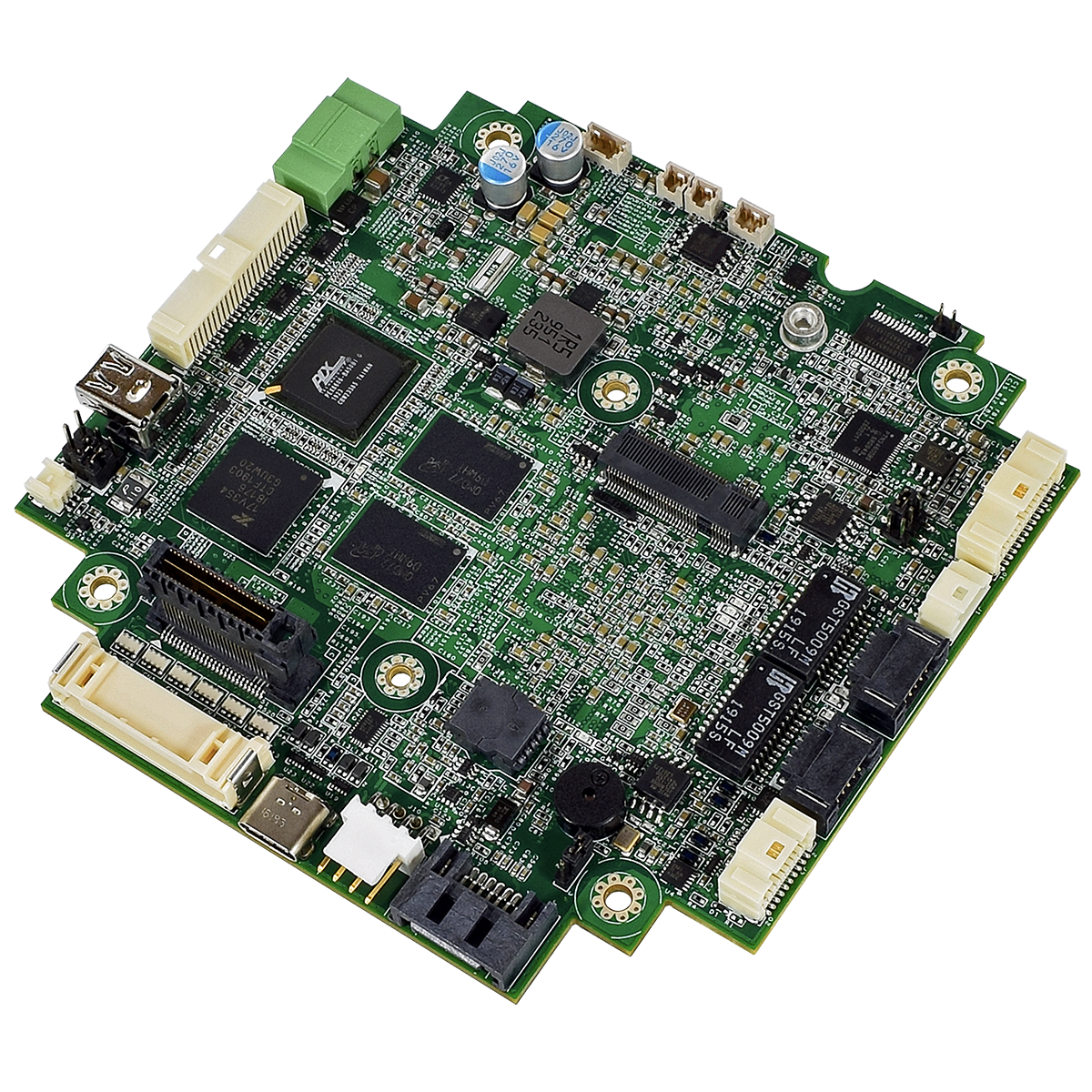
The PXI-C441 includes up to 8 Gbytes of soldered down LPDDR4 system memory and a non-removable eMMC device for solid-state storage of an operating system (OS) and applications. In addition, the board supports M.2 and SATA devices. The SBC’s rugged design and extended operating temperature range are what suit it for Industrial IoT (IIoT) applications and embedded systems in the industrial control, transportation, and energy markets.
Returning to the security question, in the early days of large-scale computer systems, most attacks came through the software, due to the simple fact that many of the OT systems were not connected to the Internet. That’s changed obviously, and the IIoT is getting smarter (and closer to the IT) than ever before. Part of the change is due to developers having done a relatively good job shoring up the software. And the other part is hackers are getting far more sophisticated.
Maintaining control of a company’s physical assets to ensure their safe operation at all times is one of the primary objectives of OT cybersecurity. Very simply, a facility must be designed and maintained to operate safely.
The Meshing of IT and OT
The IT and OT worlds are now so closely intertwined that it’s difficult to see where one ends and one begins. When the IIoT is involved, data often comes from the Edge, where the OT equipment resides. It gets to the IT, which can be the Cloud, where the data is stored and analytics are performed. Then it goes back to the OT infrastructure so an action can occur. For these reasons, security measures must include both IT and OT equipment.
While an IT hack usually involves the theft or destruction of data, an OT breach typically has more to do with affecting physical assets—taking control over, shutting down, or altering equipment or machinery processes.
IT security generally focuses on protecting access to the network, and all the devices and networks (and information) connected to it. But as the IIoT evolves, the equipment evolves with it. The result is more endpoints. In many cases, that endpoint is some type of sensor. Each one of those endpoints/sensors is also a potential entry point for a hacker.
The security teams for both the IT and OT must be proactive and not just reactive, although being reactive is often required. Strategies and techniques to secure systems continue to evolve, making it more difficult for hackers.
The bottom line is that both your IT and OT infrastructures must be secured from malicious actors. A weakness in either IT or OT will end up bringing down both. The experts at WINSYSTEMS, along with their robust ecosystem of technology partners, can help you design and deploy embedded solutions that are equipped to resist cyber-attacks.
