
The Federal Information Processing Standard, also known as FIPS (Standard 140-2), is a U.S. government computer security standard that’s used to approve cryptographic modules. That comprehensive standard has also been adopted by the Canadian government. It dates back to the early 2000s but is still a specification that OEMs look for when putting their systems together. The standard specifies what security requirements must be satisfied by that cryptographic module, and it covers a wide range of applications including medical, and many areas of design, including the ports and interfaces.
The FIPS standards specify the best practices and security requirements for implementing crypto algorithms and encryption schemes. They also delve into working/interacting with various operating systems, parts of the hardware, and firmware, basically whenever and wherever sensitive data is being used. Note that this only applies to non-military systems. In addition, FIPS defines specific methods for encryption and specific methods for generating encryption keys.
While FIPS 140-2 was initially intended for regulation in just the U.S. and Canada, the standard gained wide popularity in Europe, Australia, and other countries. Outside the US and Canada, some countries have adopted a Common Criteria (CC) that does essentially the same thing as FIPS. And in cases where there are gaps in the CC standard, the fallback specification is FIPS, as it is more encompassing than other similar standards.
There are four levels of FIPS 140-2 validation, ranging from Level 1 to Level 4. Note that Levels 1 and 2 are quite common, but the same can’t be said for Levels 3 and 4. The security level that’s required for a system could potentially affect the time it takes for design, simply because designing to the higher levels add complexity, hence require more time.
Level 1 is the most basic security level, and ensures only standard encryption algorithms. Level 2 validation takes the next step as it looks for tampering and other hardware level malpractices.
Level 3 prevents unauthorized access to the system’s critical security parameters (CSPs). Because the security mechanisms increase as the levels increase, detecting and responding to a threat is more likely. Security measures may include stronger enclosures, and/or tamper-detection/response circuitry. Level 4 offers the most modern defense available to ward off cyber-attacks. Here, the detection of penetration leads to the immediate deletion of all plaintext CSPs.
Along those same “secure” lines, in 2011, the Department of Defense (DoD) created its Information Network Approved Products List (DoDIN APL) to identify solutions that were tested and are able to address government security concerns. The list represents the agency’s master list of products available for purchase that it deems as secure, trusted, and approved for deployment within the DoD’s technology infrastructure.
At this point, you’re probably asking yourself how all this FIPS talk fits in with WINSYSTEMS. I’m glad you asked. First, we recommend that if you’re in need of a secure system (and who isn’t?), that you partner with an expert for design validation prior to submitting your product for certification. Second, make sure that your partner has experience helping clients improve security so their end products can be certified for FIPS compliance or whatever type of security is needed for the intended application.
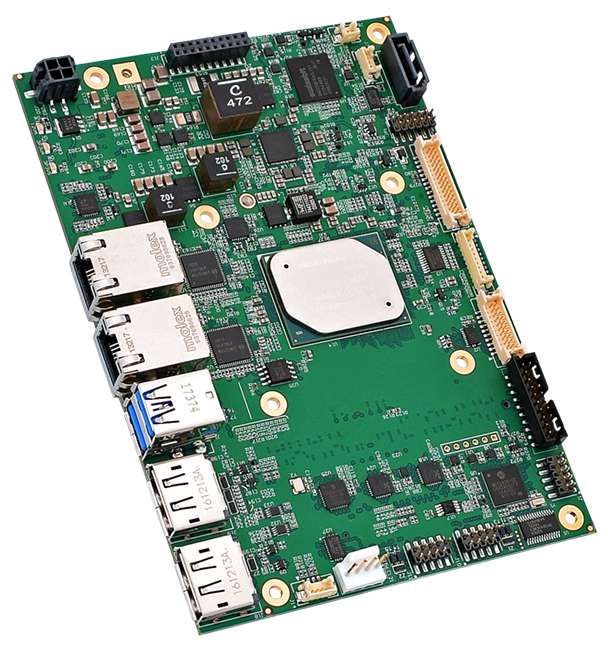
Aimed at applications that require higher levels of security, the WINSYSTEMS’ SBC35-427 is an industrial single board computer that’s designed with Intel’s Apollo Lake-I E3900 series of microprocessors. It can house an Atom x5-E3930 dual-core processor, running at up to 1.8 GHz; an Atom x5-E3940 quad-core processor, also running at up to 1.8 GHz; or an Atom x7-E3950 quad-core processor, running at up to 2.0 GHz.
The SBC35-427’s combination of off-the-shelf functionality, multiple expansion and configuration options, and operational temperature range of -40°C to +85°C suit it for industrial IoT applications. Other features include three simultaneous display outputs, two 10/100/1000 Mbps Ethernet ports, six USB 2.0/3.0 interfaces, and a host of additional I/O.
The bottom line is that the standards bodies are taking a very serious approach to security. You should follow suit.
