Rugged highly reliable embedded computing solutions
Grand Prairie, TX – June 23, 2025 – WINSYSTEMS, a leader in rugged embedded computing solutions, proudly announces the addition of two new high-performance embedded computers to its small form factor product lineup: the SBC-472-TS570 and SBC-477-TS570. These new models build upon the proven reliability of the SBC-472 and SBC-477 families, while featuring a more… Read More »
Read More >Prototyping ensures that all stakeholders in a product’s success have a clear picture of the (nearly) finished product. It allows software testing to occur on real hardware. And it lets the design team focus on the user interface. Implementing these steps concurrently results in a faster time to market and fewer design changes along the… Read More »
Read More >If you’re a regular reader of this blog, you know that we have covered many board specifications, form factors, standards, and so on. For the general embedded computing market, we’ve covered just about all the mainstream standards. The tip of the iceberg reveals such standards as EPX, EPIC, 3.5-in., PC104, and multiple variations of ITX…. Read More »
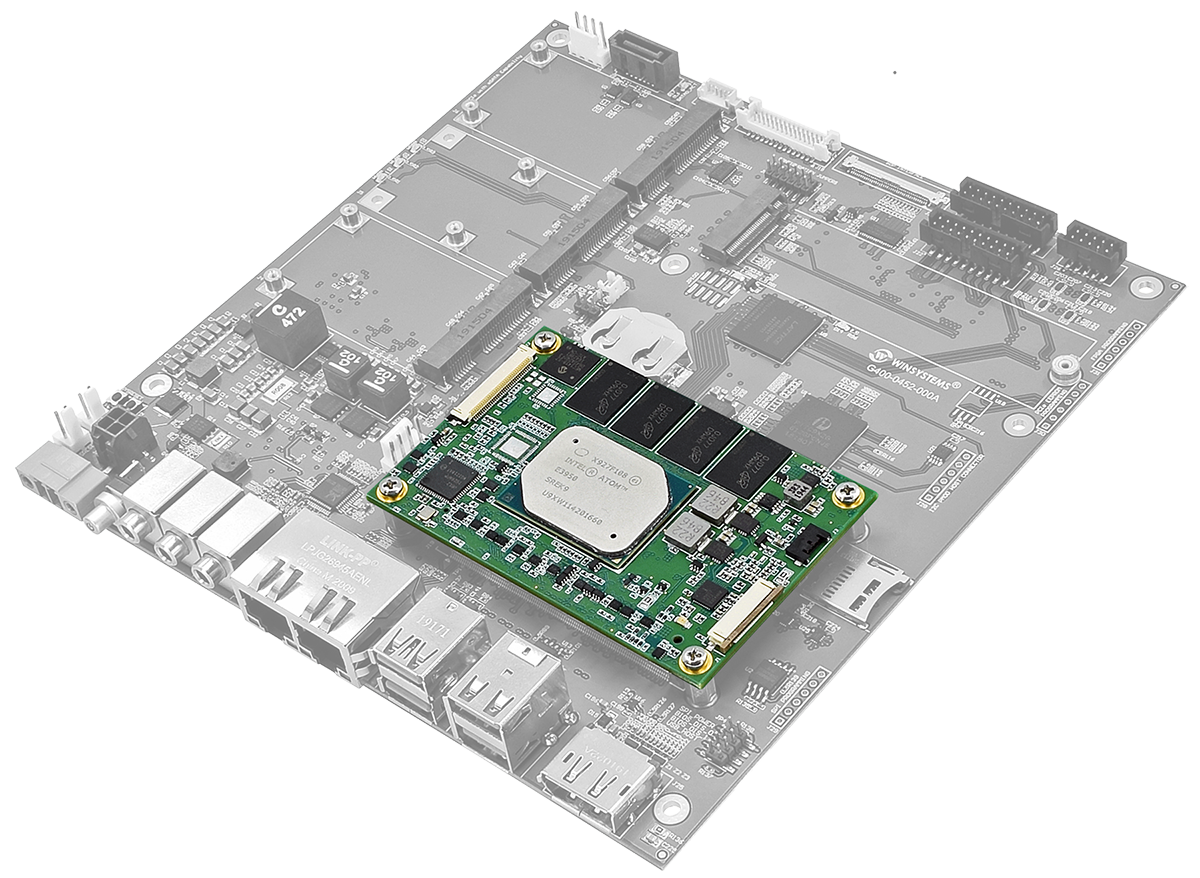
Read More >COMs are essentially embedded computers built on a single circuit board. What differentiates the COM from a conventional single-board computer (SBC) is that it lacks the standard connectors needed to directly connect external I/O devices. Hence, the module would be mounted onto a carrier card or baseboard that breaks the system and I/O buses out… Read More »
Read More >